What is Quantum Key Distribution, and How Does it Work?
8 min read
Summary
Quantum Key Distribution (QKD), one of the best examples of quantum cryptography, is a technology that relies on principles of quantum mechanics to facilitate the exchange of a cryptographic key between two remote parties.
Subsequently, the exchanged key can be securely used with conventional cryptographic algorithms. QKD provides absolute security guaranteed by fundamental laws of physics, while classical cryptography systems rely on potentially crackable mathematical algorithms.
Such a radical approach has earned its name as the future of network security. How does it work, and how can it help companies overcome ever-increasing privacy and security concerns?
How it actually works
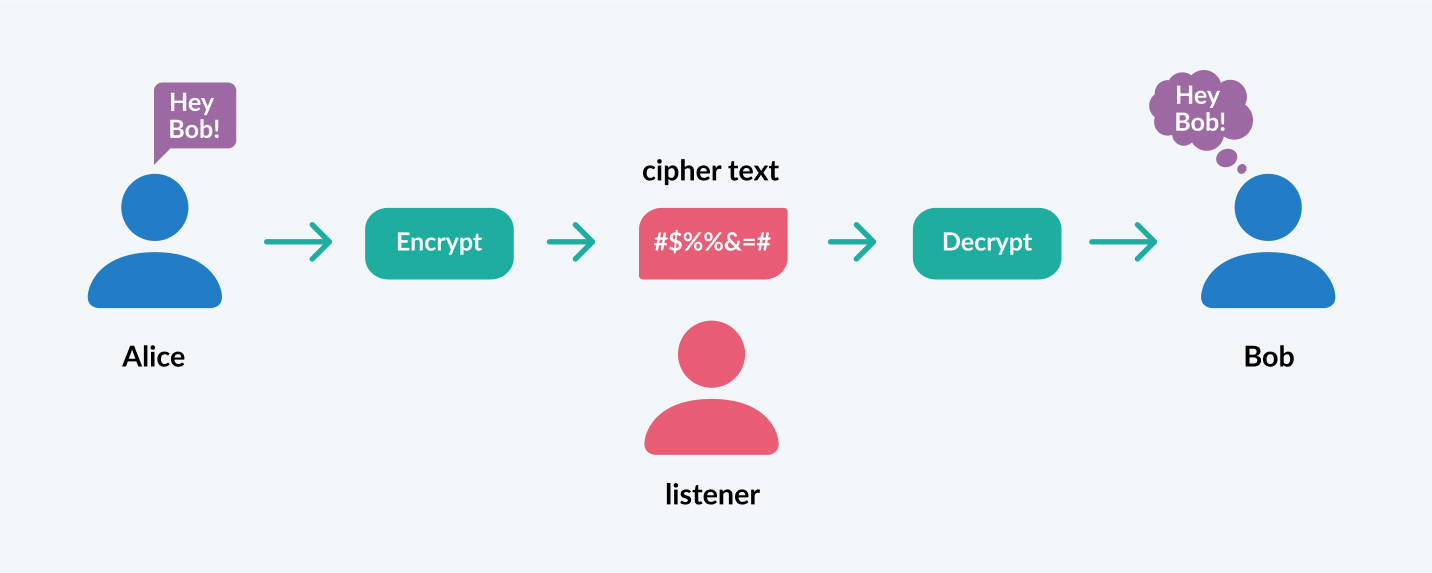
Let’s see how this works using an example with some familiar names. If two parties – Alice and Bob – want to communicate securely over an insecure channel, they have to agree on an encryption key before starting their conversation. Normally, they would use some of the commonly accepted asymmetric cryptography algorithms to exchange the key, and then use that key to encrypt their messages.
However, the advent of quantum computing poses a big threat to asymmetric cryptography as the mathematical problems that asymmetric cryptography is based on could be solved by a sufficiently powerful quantum computer using Shor’s algorithm.
Although they’re often confused, QKD and quantum computing are two very different things. The term “quantum computing” refers to the use of quantum mechanics to perform computations. Quantum computers are fundamentally different from classical computers, which are based on binary or two-state systems. As a result, quantum computers can potentially solve problems that classical computers cannot. For more on quantum mechanics, see our article here.
QKD eliminates the quantum threat because it doesn’t have its basis in mathematics but in quantum mechanics. Alice and Bob exchange a key using polarized photons – particles of light with a specific property – over the insecure channel using an agreed-upon protocol such as BB84 or E91. The photons are then received by Bob, who measures the photon polarization and builds the secret key based on the reading. This measurement “collapses” their quantum states and later allows him to encrypt his messages with the key.
The science behind “spooky action”
Quantum mechanics study physical phenomena at the atomic and subatomic levels, which is quite different from classical physics. An important concept related to QKD is entanglement. It occurs when two or more particles are correlated in such a way that an action performed on one particle immediately affects the other particle – even if they’re separated by a distance. This phenomenon was first called “spooky action at a distance” by Albert Einstein but is now accepted as true by physicists.
The other important concept behind QKD is the quantum indeterminacy principle, which states that the mere observation of a quantum object disturbs it in an irreparable way. This principle is used to guarantee the absolute security of QKD, because, in order to intercept the key, the eavesdropper must observe it, which inevitably collapses the state and introduces errors in the transmission. It’s important to know that only after the transmission do we find out whether the communication was intercepted or not. Therefore, this technology is used only for the exchange of the secret key, but not for the exchange of valuable information.
The benefits
QKD has many benefits over traditional key distribution methods. First, QKD is more secure than traditional methods because it is impossible to clone the quantum state of a particle. This means that an eavesdropper cannot copy the key without being detected and read the encrypted message. Second, QKD is arguably more efficient than traditional methods because it does not require multiple rounds of communication to establish the key. Finally, QKD is more robust than conventional methods because it can detect eavesdropping attempts.
An abundance of applications
Initially developed for military use in the 1980s, QKD has since been adopted by other industries as well. Today it can be used for secure data transmission in any industry, including banking and finance, healthcare, defense, intelligence agencies, education institutions, etc.
1. Data centers and cloud computing
Data centers store and process a large amount of data. They also transfer data from one server to another, and various malicious attacks can compromise the security of sensitive data in transmission. With the rapid advances in fiber-based QKD, secret keys can be generated using standard telecommunication devices. These secret keys can then be used to secure data centers by providing quantum-safe encryption for data transmission between two or more data centers. Data transmitted to high-performance computers for processing can also be secured using the secret keys generated by QKD. In addition, QKD can also be used as a cloud service where quantum-safe secret keys are distributed from servers to end users on demand.1
2. Post-5G network era
With the proliferation of 5G mobile devices, QKD can be used to secure the 5G network and beyond by securing the link between the base station and the 5G core network, as well as the link between the base station and the user, to enable quantum-safe end-to-end voice, text, and data communication services. In addition, software-defined networks used to manage 5G networks can also be used to manage QKD connections and QKD applications beyond 5G networks2. Find out more on software-defined networks in our article here.
3. Internet of Things (IoT) and Mobile Edge Computing (MEC)
The threat of malicious attacks will increase with the large number of devices and sensor nodes deployed in the IoT networks. IoT devices collect sensitive personal data through, for example, location tracking and video surveillance. The security and privacy of the data collected by IoT sensors can be enhanced using secret keys generated with QKD. Since IoT devices have limited power and computing capacity, IoT controllers must distribute the secret keys to the edge devices. The devices can then use the secret keys to encrypt the data before sending it to a central data processing center. In this context, secret keys generated with QKD can improve the security, privacy, and sovereignty of low-latency MEC services.3
4. Government and Banking
Data security and sovereignty are paramount for government agencies and the military to protect critical national data such as defense secrets, intellectual property, and citizen data from hackers. QKD will play an important role in securing critical national data in a quantum-safe manner. In this context, QKD can be used to secure private communication links between different government agencies to exchange confidential data. In addition, the secret keys generated using QKD can be used by the banking sector for secure ATM transactions, online credit card transactions, and securing customer data stored in bank data centers. Government agencies and banks can establish a trusted repeater-based local quantum network to enable QKD-based end-to-end encryption.4
5. Smart Grid and National Pipelines
Smart grids and national pipelines used to transport oil and gas are the backbones of any country’s economy. Therefore, QKD can play an important role in securing the smart grid to prevent power outages and protect national pipelines from hackers. To this end, QKD can be used to secure communications at the physical layer to protect the smart grid from malicious attackers.5
6. Healthcare
Telemedicine and e-healthcare services have become an important part of healthcare due to the pandemic. Therefore, using the secret keys generated with QKD may be extremely important to secure the storage, transmission, and processing of sensitive patient data. In addition, various biosensors are now built into smartwatches and other wearable devices that collect and transmit personal health data and the user’s daily activities. These devices store the user’s health status and use it to predict any serious medical problems for the user. The unconditional security and confidentiality of this intimate health data in the age of quantum computing can be ensured by using QKD-based encryption methods.6
Conclusion
In conclusion, quantum key distribution provides a number of benefits over traditional methods of key distribution, including increased security and privacy, and the ability to distribute keys over long distances. Additionally, quantum key distribution is resistant to eavesdropping and immune to many attacks.
Michel Roethlisberger, CEO & Co-founder of InnoBoost
“As it stands, QKD is the only possible response to counter the security attacks to come with the advent of quantum computing.’’
InnoBoost is an IBM Platinum business partner, a level reserved for partners who deliver high-value transformative solutions and achieve the highest levels of customer satisfaction, technical and sales certifications, and sales success.
We are proud to have been early adopters of technology when ID Quantique launched, thus building solutions on top of it. Our current project with them is securing data transfers between data centers.
Our skilled, agile, and certified team prides itself on delivering an unparalleled experience to its customers. We ensure a seamless business transition from system and solution design to configuration, from price negotiation with IBM to ordering and delivery tracking. We also arrange access to other partners and consultants as needed.
Contact us today. Let’s look at your current situation and find out how we can help you improve your business!
123456 “Towards the industrialisation of quantum key distribution in communication networks: A short survey”Ruiqi Liu,Georgi Gary Rozenman,Neel Kanth Kundu,Daryus Chandra,Debashis De, June 2022.
You may also like…
Unlocking the Power of Custom AI with InstructLab
5 min readSummary In the dynamic landscape of artificial intelligence, the ability to create models tailored to unique business needs is more than a competitive edge—it's a necessity. InstructLab, a collaborative initiative from IBM and Red Hat, is revolutionizing AI...
Strengthening Authentication in the Digital Age with IBM Verify
5 min readSummary In today’s interconnected world, the importance of robust authentication systems cannot be overstated. As digitalization accelerates, safeguarding sensitive data and critical systems has become a top priority for businesses. Effective access...
From Data Chaos to Data Confidence: Real-World Use Cases of IBM Data Product Hub
5 min readSummary In a world where data streams in from every direction—transactions, patient records, supply chain logs, and more—businesses often face “data chaos.” Instead of powering innovation, their data sits scattered in different formats and systems, making it...